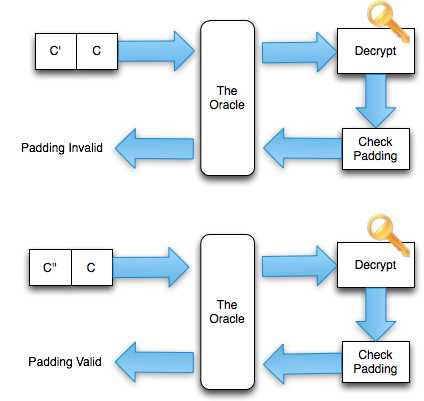
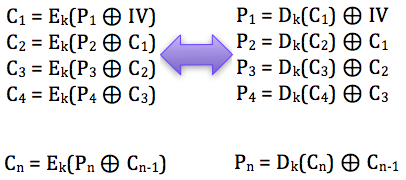http://localhost:8888/kripto/thematrixoracle.php?crypted=2D7850F447A90B87123B36A038A8682F
When the URL is opened, the ciphertext is sent to the server in the parameter, then the server will be crypted gave a response:
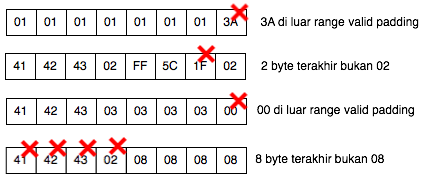
' 500 Internal Server Error ' when paddingnya is invalid.
' 200 OK ' if paddingnya is valid.
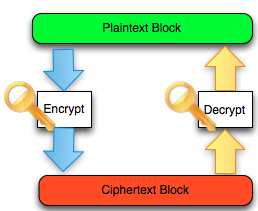
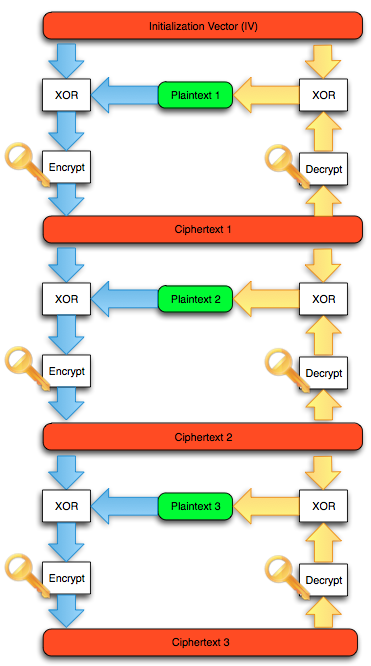
Block
cipher algorithm used is DES 64 bit sized in CBC mode (cipher block
algorithm-any used is not important, padding oracle attack attack the
CBC mode block cipher algorithm-any used). In this scenario the source code used in the oracle server is:
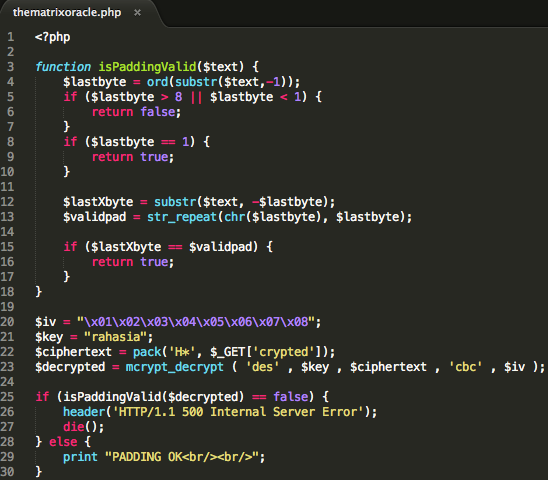
Without
knowing the key, just use the answers from the oracle, how does the
Internet Cafe customers last for mendekrip the content parameter of the
crypted?
Get the last byte of P2
Now it's time attack padding oracle. We'll try mendekrip C2 one byte per byte, starting from the last byte and then advanced to the first byte.
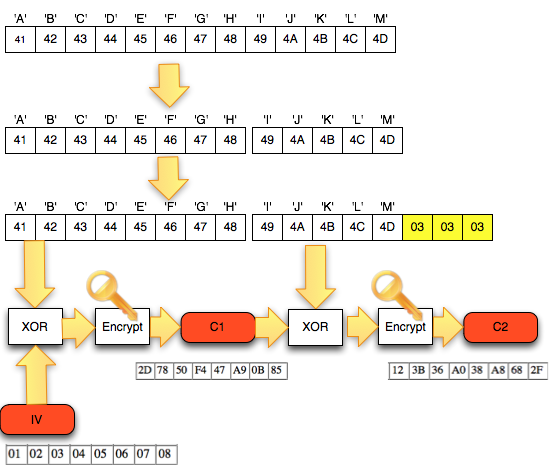
The first thing to do is to break ciphertext which is found from the browsing history above, into the blocks. Because
of the length of the parameter on the URL crypted is a 32 byte string,
meaning that the length of hexa is 16 bytes, then it could be presumed
that this is a block-cipher with a block of length is 8 bytes.
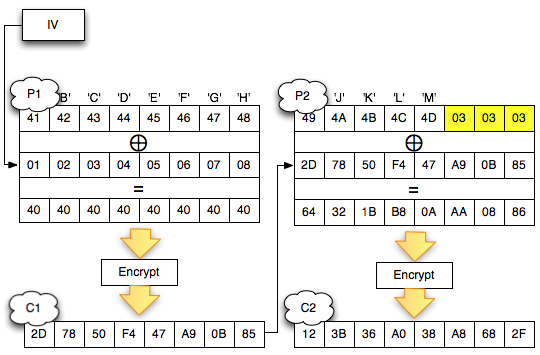
Next was break up the ciphertext into the block. Once broken down into 2 blocks, obtained C1 = ' 2D7850F447A90B87 and C2 = '/123B36A038A8682F '. This is the block C1 and C2 of the original found in the URL of the browsing history.
We begin with the last first block C2 mendekrip (' 123B36A038A8682F '). As already mentioned earlier, we would have to send two ciphertext blocks into ' the oracle ':
- The first block is a block of ciphertext custom made attacker. This
block of bytes originally could contain anything (random or null byte),
the important thing is the last byte that affects padding should be
sought by means of brute force to create padding to be valid.
- The target block will be didekrip (' 123B36A038A8682F '). This block is fixed in each request because this will block didekrip
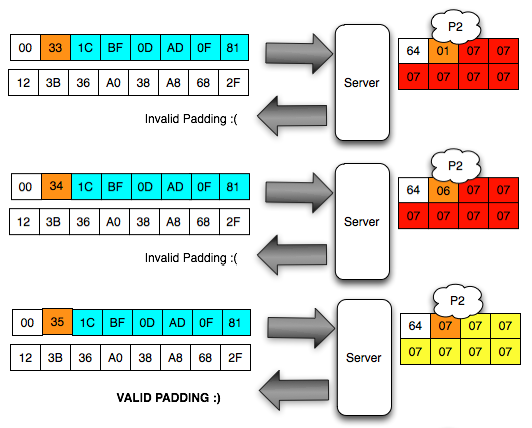
Two examples of the block cipher that is sent to the server is like below.
In
the picture above we use the row of 7 null bytes (byte 00) and one last
byte for brute force ranging from 00 to FF, for ciphertext blocks
first. Whereas the second block remains unchanged during the brute force because it is the target that will block didekrip.
The two ciphertext blocks in the picture above towed then sent to the server. Server
as ' the oracle ' will mendekrip the ciphertext block 2 and give a
response would produce the plaintext with a valid or invalid padding.
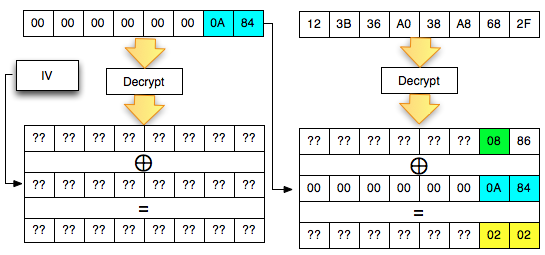
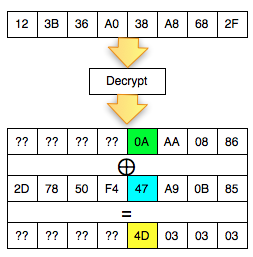
We will start from the last mendekrip C2 byte, then get a byte by one byte until the first byte C2. Because
you're looking for is the last byte of P2 (decryption C2), then we have
to find the last ciphertext block of the first byte that make P2 be
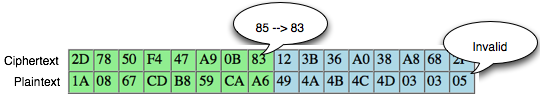
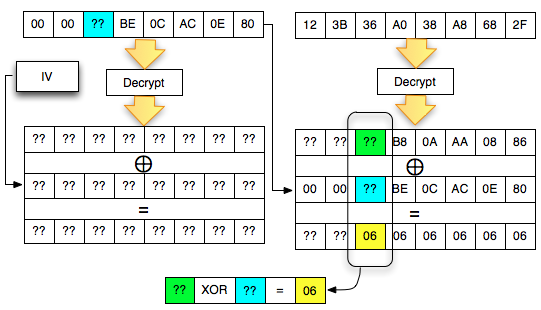
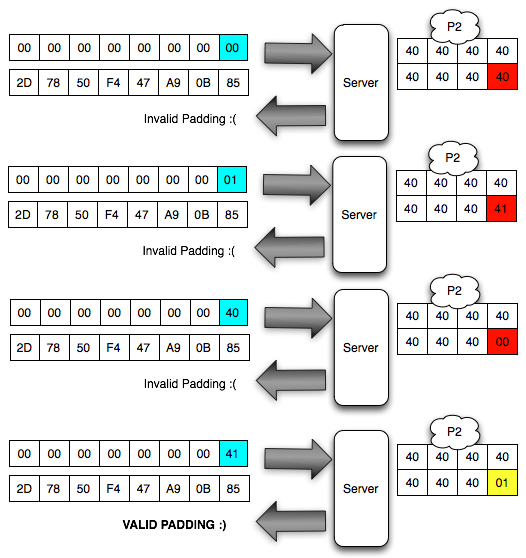
worth 01 (invalid padding). The situation is reflected as in the picture below.
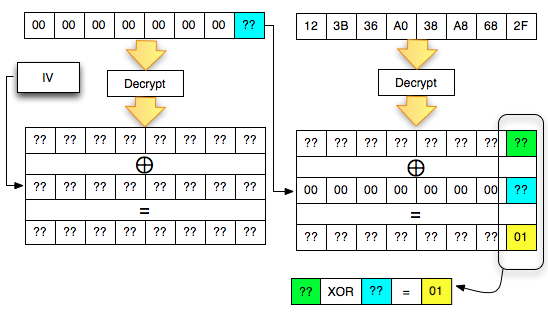
In
the picture above, there is one equation but with two unknown
variables, A XOR B = 01, should this equation cannot be solved. But fortunately we've got ' the oracle ', he's going to help us solve the equation. How do the trick?
We
can interrogate ' the oracle ' by trying all possible B ranging from 00
to FF because it is between 00 and FF there must be BS that makes ' A
XOR B = 10 ° to right. We could ask ' the oracle ' to the following questions:
Will A XOR 00 = 1?
Will A XOR 01 = 01?
Will A XOR 02 = 01?
Will A XOR 03 = 01?
Will A XOR 04 = 1?
Will A XOR 05 = 01? dst
When
' the oracle ' replied with ' invalid padding ', it means to answer the
above questions is ' no ' and we have to ask the question to the next
byte to FF. Instead when the oracle answered with ' invalid padding ',
meaning that it answers the above questions is ' yes ' and we've managed
to find the B.
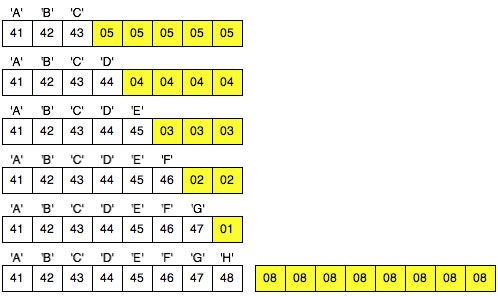
Brute Force Was The Last Byte
To
make it more clear let us look deeper process of brute force to get the
last byte of C1 makes the P2 became the last byte is 01 so that
paddingnya is valid.
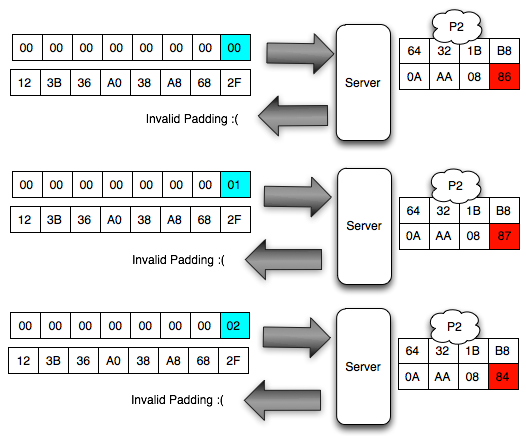
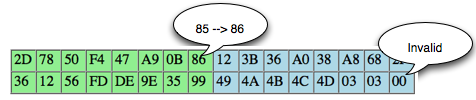
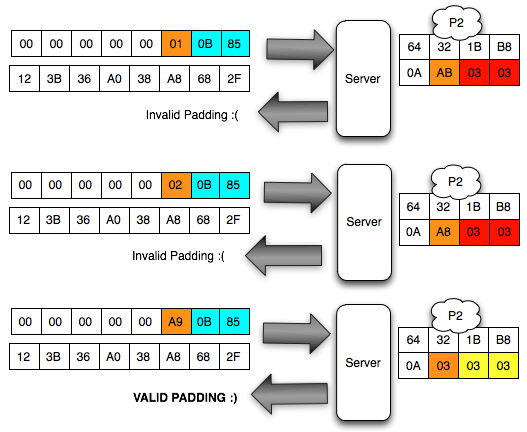
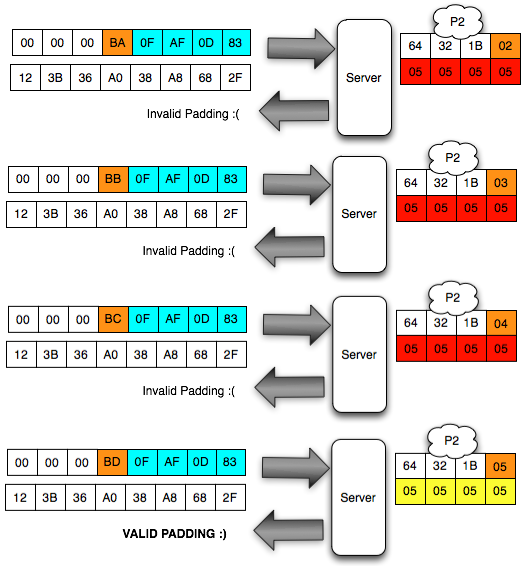
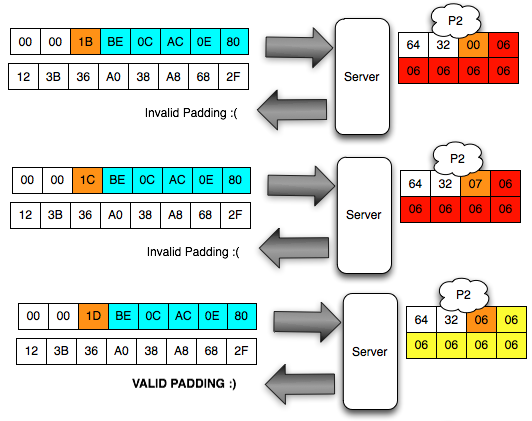
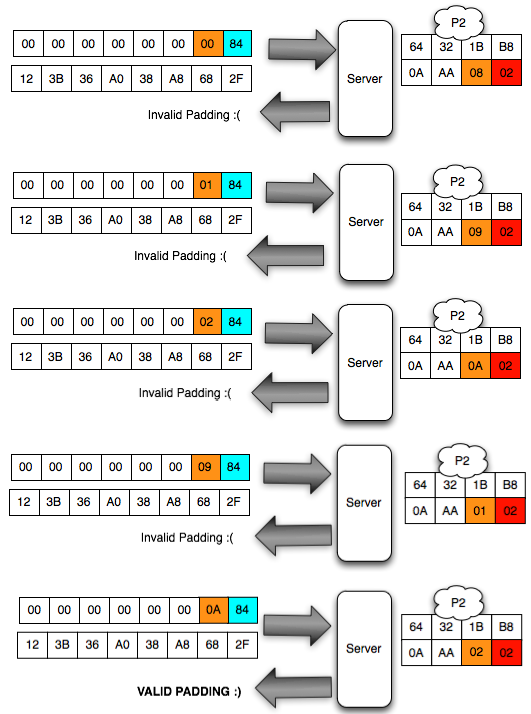
In the picture above look client sends the ciphertext 3 variants. In
the first variant, the last ciphertext block of the first byte is 00,
after mendekrip this ciphertext, ' the oracle ' was answered with '
invalid padding '. When sending a ciphertext, in
fact we are currently interrogating ' the oracle ' with the question '
what is A XOR 00 = 1? ', and it turns out the answer is ' no ' so we
should try with another question.
The Client does not know the decryption ciphertext which she tell be what. The Client can only be guessing based on the response from ' the oracle '. Because responsnya is invalid padding, suspect and sure that client bytes last definitely not 01. Even
though the client had no idea what, but decryption results client know
that the last byte is 01, certainly not information-leak as small as
that alone is enough to mendekrip ciphertext without knowing the key.
In
the second variant, the last ciphertext block of the first byte is
raised to 18, but the answer ' the oracle ' is still the same, i.e. '
invalid padding ', meaning decryption results certainly not end with 1
byte. This time we asked the question ' what is A XOR 1 = 1? ', it turns out the answer is still ' no '.
In
the third variant, the last ciphertext block of the first byte is
raised again becomes 02, but still also answer ' the oracle ' is '
invalid ' padding. In this request we ask the question ' what is A XOR 02 = 01? ', unfortunately the answer is still ' no '.
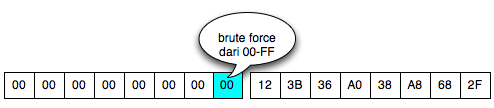
The
Client should continue to try to raise the last ciphertext block of the
first bytes of 00 to FF because it is between 00 and FF there is
certainly one that generates a status byte padding. The
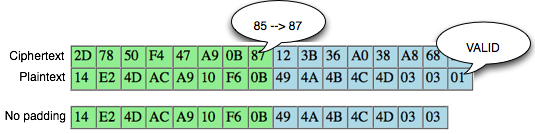
image below of the brute force process above until finally the client
discovers that the last byte is 0 × 87 will make the status of padding
to be valid.
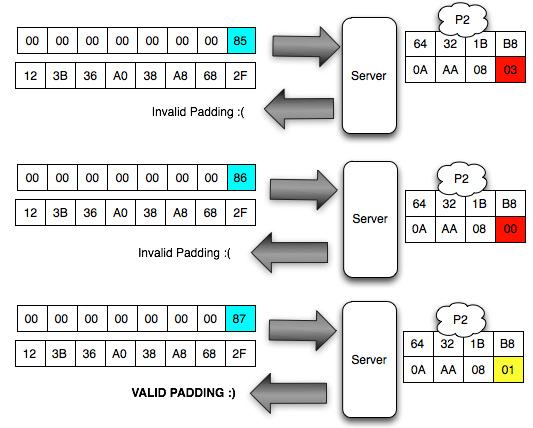
Hooray, after trying the byte 00, finally on request to 88, it brings that last byte is generating valid response 98 padding. This time we got an answer ' yes ' from ' the oracle ' to the question ' what is A XOR 87 = 01? '.
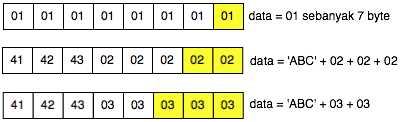
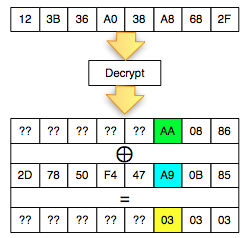
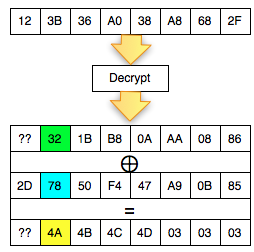
Once the can is valid padding, so what? In
fact there is something cetar formations here, let's look at more
details more bytes per byte of what happened (Bytes that contain '?? '
meaning is not known of its contents by the client).
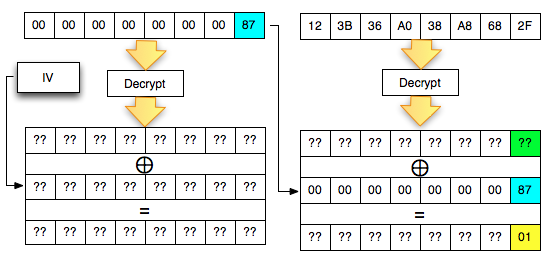
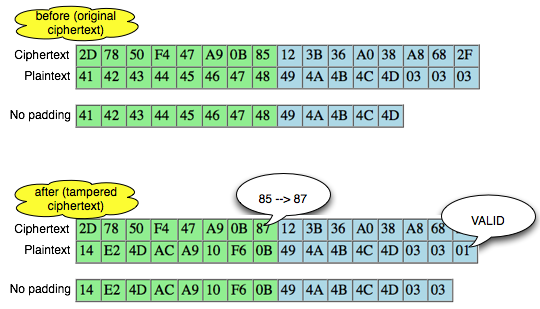
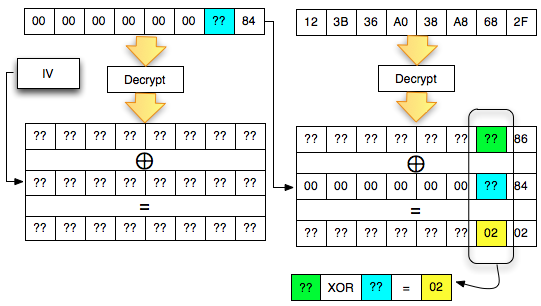
The picture above is important to understanding the padding oracle attack. We look back on what happened.
- Client sends 2 blocks with the last ciphertext block of the first byte value 0 × 83
- Mendekrip ciphertext from the client Server
- After the last byte of value turned out to be didekrip 01 (valid padding)
- The Client detects the response from the server that the padding is valid
- Because
of the padding is valid, the client suspected (and believe) that the
last byte of ciphertext decrypted results that he send is 01
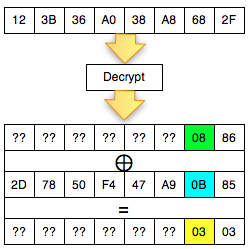
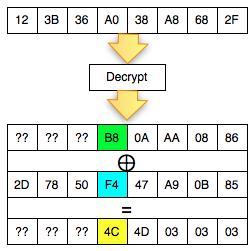
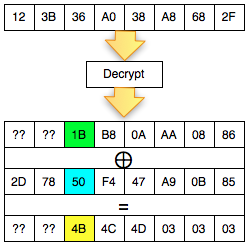
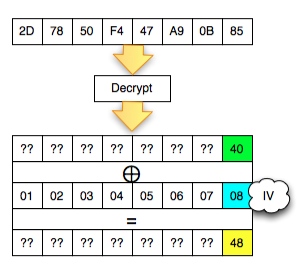
Okey, so far only the client knows the bytes 0 × 87 and byte 0 × 01, what could be obtained from it? The answers are in the picture above, we call it green byte as A.
From the previous equation ' the oracle ' answered ' yes ' to the question: is A XOR 0 × 81 = 0 × 01. Previously this equation had two unknown variables, now live one, which means that this equation can be solved. Then what is A?
The answer is easy, A is 0 × 87 ⊕ 0 × 01 = 0 × 86. Hooray! By detecting invalid padding/no response from the server, the client can now find out A is 0 × 86, but wait, A what? The answer is also in the picture above.
In the picture above is clear, A green is the last byte of the Decrypt (C2). But
don't keburu happy first, remember that Decrypt (C2) not P2, there is
still one more step to be P2, still needs to be used with a C1 XOR to
make P2.
Because the last byte C1 is 0 × 85 so that we can get the last byte of P2 is 0 × 86 XOR 0 × 85 = 0 × 03
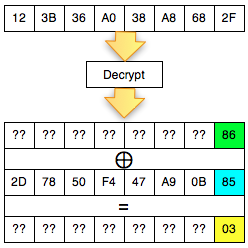
Get byte 7 P2
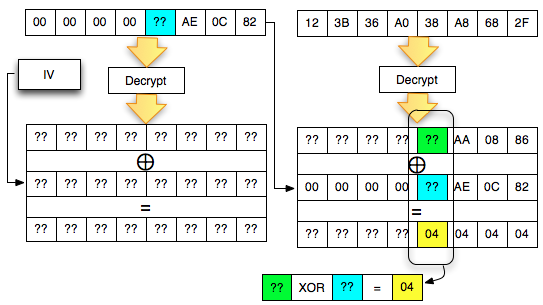
After successfully getting the last byte of P2 is the next mendekrip 1 bytes before the last byte.
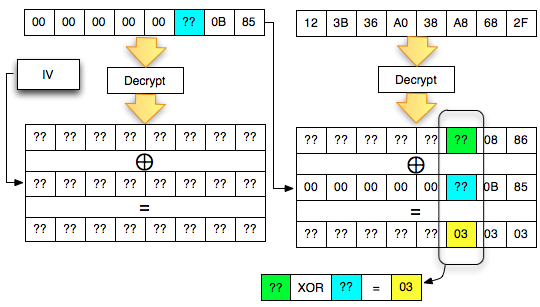
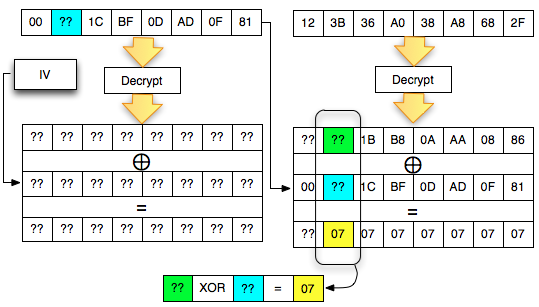
The trick is similar to the previous, i.e. by making that padding decryption ciphertext sent client, to be valid. But a bit different than before, this time the desired conditions of valid padding is syllabic byte 02-02. The situation is shown in the image below.
Why is the last ciphertext block of the first byte is we set contains 0 × 84? In the picture above, it is clear that 0 × 86 XOR something = 0 × 02, then something that is 0 × 84, simple math).
Now
live the last byte before still do not know how to generate required 0 ×
02 because there are two question marks there, so if the written
equation: A XOR B = 21, what is A and B?
An equation with two variables is not known should not be completed. How
to find A and B equals before, we'll interrogate ' the oracle ' to help
solve the equation in the form of brute force as follows:
- Will A XOR 00 = 2?
- Will A XOR 01 = 02?
- Will A XOR 02 = 2?
- Will A XOR 03 = 02?
- Will A XOR 04 = 02?
- Will A XOR 05 = 2? dst
Once
again, the brute force that we do with many variants of the ciphertext
essentially interrogate ' the oracle ' to help solve the equation above.
If ' the oracle ' respond with a status of '
invalid padding ' that means the answer to the above questions is ' no
', meaning that it should try with the next question. When ' the oracle ' respond with a status of ' invalid padding ' that means the answer to the above question is ' yes '.
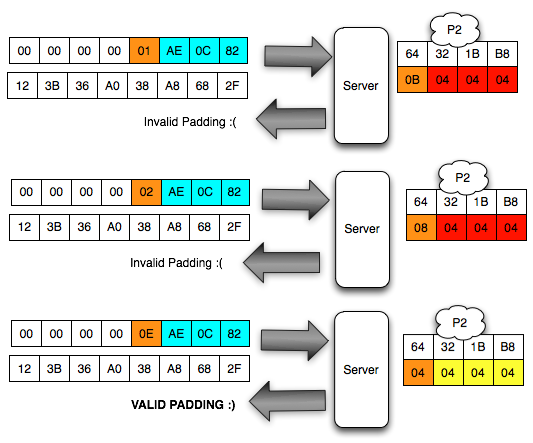
The image below is a picture of the brute force process is done.
After dibrute force ranging from 00, status valid obtained when 2 padding bytes of value last 0A -84. Back
again into the above equation, the answer to this same status valid
padding means that with the answer ' yes ' to the question ' what is A
XOR = 0A 02? ' so that A can be calculated easily, that is XOR = 0A 02
08. The situation is now becoming like the image below.
The contents of the byte of P2 now can already count i.e. 08 XOR 0B (0B is 7 bytes of the original C1) = 03.
Get the 6th byte of P2
This
time the client should send the two ciphertext blocks such that when
didekrip on the server, the result is a P2 with the last 3 bytes
containing 03-03-03. The situation now is like the picture below.
In
the figure above, the two last ciphertext block of the first byte is
stuffed with 0B -85 to ascertain when the last byte diXOR produces 2 P2
03-03. Now the 6th byte should be sought by means of brute force, interrogate ' the oracle ' to solve the equation A XOR B = 03. Brute force process to get a valid padding shown in the image below.
After
gaining the status of valid padding, meaning we've got the answer ' yes
' to the question ' what is A XOR A9 = 03 ° so that it can be counted A
is 0xAA. The 6th Byte of P2 is true 0xAA 0xA9 XOR (A9 was the 6th byte of the original C1) = 0 × 03. The situation now is like the picture below.
So far we've managed to get the last 3 bytes of the decrypted result, i.e., the Divisione 03-03-03.
Get the 5th byte of P2
Get
the 5th byte is also done by sending two block cipher such that when
didekrip on the server generates a valid padding with final byte
04-04-04-04. The situation is like the image below.
The
first three bytes of the last ciphertext block contains AE-0 c to
ensure that the Eagle when it generates the last 3 bytes diXOR P2
04-04-04, interrogate ' the oracle ' to solve the equation A XOR B = 10.
Brute force process to get a valid padding shown in the image below.
After
gaining the status of valid padding, meaning we've got the answer ' yes
' to the question ' what is A XOR 0E = 10 ° so that we can calculate A
i.e. 0A. After getting the 0A, we can calculate the 5th byte of P2 are original, that is XOR = 4 d 0A 54. So far we've got are reflected below.
Get the 4th byte of P2
Get
the 4th byte is done by sending the two ciphertext blocks such that
when didekrip on the server generates a valid padding with the last byte
05-05-05-05-05. The image below illustrates the situation.
Brute
force manner similar to before, note that when the 4th byte of the
first ciphertext block contains the response from the server 0xBD, is
padding.
By
obtaining valid padding status means that we got an answer ' yes ' from
' the oracle ' to the question ' what is A XOR BD = 10 ° so that A can
be calculated i.e BD 05 = XOR B8 and the 4th byte of P2 be B8 XOR F4 = 4
c. The picture below shows the current situation.
3 more!
Stay 3 bytes again yet. Let's continue. Get the 3rd byte of P2 is done by sending a ciphertext block makes 2 6 bytes of the last P2 became the 06-06-06-06-06-06.
We must membrute force of the 3rd byte C1 ('?? ' blue cyan) to get a response from ' the oracle ' that the padding is valid. When
getting invalid padding, the client can be sure that the 3rd byte of P2
is worth 20 so that the last 6 bytes being 06-06-06-06-06-06.
By
obtaining valid padding status means that we got an answer ' yes ' from
' the oracle ' to the question ' what is A XOR 1 d = 6 ° such that A
can be calculated that 1 d XOR 06 = 1B and 3rd byte of P2 be 1B XOR 50 =
4B. The picture below shows the current situation.
2 again!
Stay 2 more, come a little more nih! Now the client has to send the two ciphertext blocks that make P2 into 07-07-07-07-07-07-07.
The following is the process to find the brute force that produces valid byte padding.
By
obtaining valid padding status means that we got an answer ' yes ' from
' the oracle ' to the question ' what is A XOR 35 = 7 ° such that A can
be calculated that 35 XOR 07 = 32 and the 3rd byte of P2 XOR to 32 78 =
4A. The picture below shows the current situation.
Last!
Now it's time we look for the first byte of P2.
The following image is the brute force process to obtain valid padding.
By
obtaining a valid lead byte of padding is 6 c, meaning we got an answer
' yes ' to the question ' what is A XOR 6 c = 08 ° such that A can be
calculated: 6 c XOR 8 = 64. After that we can calculate the first byte, that is XOR P2 64 2D (the first byte of the original C1) = 0 × 49.
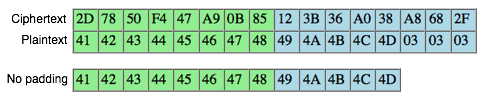
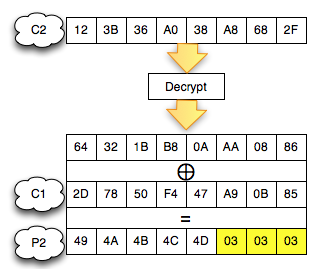
C2 Decrypted!
So
we now have been successfully C2 mendekrip (' 123B36A038A8682F ')
became ' ' + IJKLM 03 + 04 + 03 starts from the last byte to byte the
first without knowing the key and the algorithm is what is used.
Decryption
is done amazingly again not at all using the techniques of complex high
level computing (permutations, the S-BOX is not needed at all), just
XOR XOR datapun here, there manages to didekrip. So how come? This
could happen because the decrypt is a server, serverlah will perform
complex computations to ciphertext, mendekrip outside attacker stayed to
observe the response of the server as ' the oracle '.
So
it's as good as any enkripsinya algorithm, when CBC mode using and give
a response on the client are valid or invalid padding, it will be
vulnerable, although enkripsinya algorithm itself is not actually
vulnerable. Padding oracle attack attack this
instead of attacking the encryption algorithms like DES/AES, this attack
strikes the CBC operating mode.
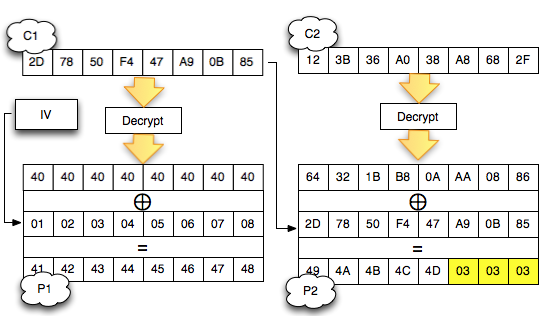
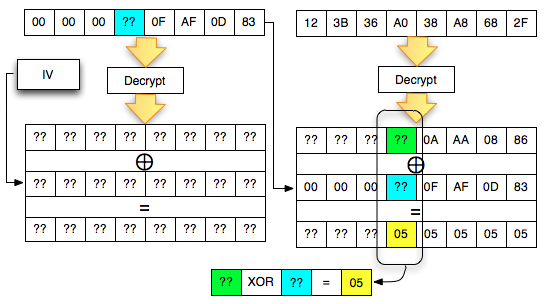
Decrypt C1
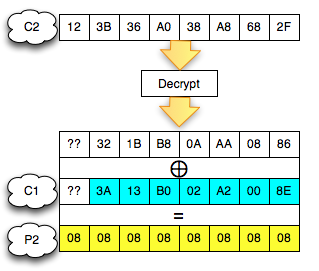
After the C2 successfully didekrip, how do I mendekrip C1 (' 2D7850F447A90B87 °)?
Same as mendekrip C2, C1 is way to mendekrip by forming two ciphertext block follows:
- Custom made blocks attacker
- Block C1 (' 2D7850F447A90B87 ') as the target to be didekrip
Then two such blocks are merged (concat) and sent to the server. Furthermore how is similar to the previous one. Here is a picture of the situation while searching for the last byte of the decryption of C1. Same
as before, the first block contains null bytes except the last byte
will be dibrute force, the second block contains a 2D-78-50-F4-47-A9-0B
-87 to be didekrip.
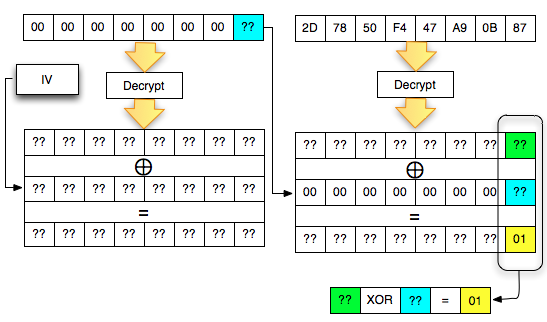
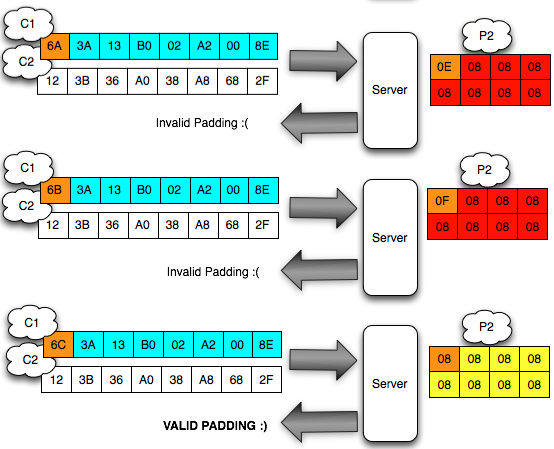
Here we start over again, departing from the last byte to byte first. We must interrogate ' the oracle ' to help solve equations ' A XOR B = 6 ° What is the A and B? The following is the process to find the brute force that makes the last valid byte padding.
After
getting a status of invalid padding means that we've got the answer '
yes ' from ' the oracle ' to the question ' what is A XOR 41 = 01 ° so
that we can calculate A is 0 × 40.
Remember to mendekrip a block, we need the previous ciphertext block. Previously
when we mendekrip our C2 to XOR-kan Decrypt (C2) results with C1, now
because we're mendekrip C1, then we need a previous block ciphertext as
well, i.e. C0 or Initialization Vector (IV). In this example the IV used is the byte array 01-02-03-04-05-06-07-08.
We
already get the Byte is 0 × 40 should we XOR it with the last byte IV 0
× 08 to get the plaintext byte last, that is XOR 0 0 × 40 × 8 = 0 × 48.
We
have been getting the last byte of the decryption of C1, the process
can continue to get byte-byte before the last byte in a way that is
similar to the previous one.